The word “IP” is something we often see and hear. Although we don’t realize it, we always use it when connecting to the Internet from our smartphones and computers. Let’s check what that IP is, how IP addresses work, and how they are used.
Furthermore, since IP addresses are individually assigned, there is a concern about the risks of personal information leaks and cyber attacks, which have become increasingly important in recent years. We will explain the basics and latest information about IP addresses.
What is IP?
IP is an abbreviation for Internet Protocol.
The Internet is a worldwide computer communication network, and the word “protocol” in English has meanings such as “ceremony, liturgy, draft treaty, protocol, agreement, and implementation guidelines”, and in the IT world, it mainly means “covenant”. There is.
In other words, IP stands for “communication protocol”. The Internet network always requires a common communication protocol for communication between devices. In IP networks, it is necessary to assign numbers to identify individual devices such as computers, smartphones, and tablets that connect to the Internet. That is an “IP address”.
What is an IP address?
IP address refers to “Internet Protocol Address”. Why do we need an IP address for Internet communication? This can be easily understood by comparing it to an exchange of letters. Of course, if you don’t know the recipient’s address, the letter won’t arrive. Address = Address is also necessary for network communication.
For example, let’s say you want to send e-mails and Zoom meetings over the Internet from a computer in the home of Mr. A, who lives in Tokyo, to a computer in the home of Mr. B, who lives in Okinawa Prefecture. First, both A and B’s computers must be connected to the Internet.
Even on the Internet network, you cannot communicate unless you can identify the other party. An IP address is like a network address that identifies devices on the network.
You can’t email or have a Zoom meeting without identifying and identifying the source and destination of your data. The number used for identification is the IP address. In other words, all devices on the network are assigned an IP address to identify them.
IP address, a number used for identification
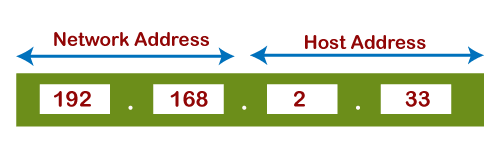
So what is an IP address? A commonly used format is something like “192.168.1.1”.
Currently, IP addresses are generally expressed as four sets of numbers from 0 to 255, such as “XXX.XXX.XXX.XXX”.
IP address notation method
We will explain how to represent the IP address below.
IPv4 address notation method
“IPv4=Internet Protocol Version 4” is the device identification number in IP version 4. 32-bit data is divided into four 8-bit data called octets, separated by dots, and expressed as decimal values.
More than 4.294 billion addresses are available from “0.0.0.0” to “255.255.255.255”. This is the most commonly used IP address on the current Internet.
■How to specifically represent IPv4 addresses For example, Yahoo! JAPAN’s IP address is “183.79.248.124”, but if this is represented in binary numbers that computers can recognize, it would be as follows.
10110111010011111111100001111100
They are called binary numbers because they are expressed using only two numbers, 0 and 1.
However, humans cannot understand this, so we convert it to decimal numbers, which humans use every day. Decimal numbers are called decimal numbers because they count up to 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 10.
To convert it to a decimal number, divide the “total 32 bit data” expressed in the binary number above into 4 parts of 8 bits each with dots.
10110111.01001111.11111000.01111100
Then convert each binary number for each dot to a decimal number, and it will look like this:
183.79.248.124
How to write IPv6 addresses
“IPv6=Internet Protocol Version 6” is the device identification number in IP version 6. This is a notation method developed based on the IPv4 address platform to overcome the limitations of IPv4 addresses.
IPv4 addresses have 32 bits of data, but IPv6 addresses can hold 128 bits of data, four times that amount. If you convert hexadecimal IPv6 to binary, it becomes 128 bits, but in this case it is “2 to the 128th power”, which means “340 trillion x 1 trillion x 1 trillion”, which means approximately 340 IP addresses can be used. That’s it.
“Kan” is a unit of 10 to the 36th power, and when actually expressed as a numerical value, it is written as follows.
Kan = 10 to the 36th power = 1000000000000000000000000000000000000
Unlike IPv4 addresses, where each 8 bit is separated by a dot, an IPv6 address is written in hexadecimal with each 16 bit separated by a colon (:=). This is stipulated by “RFC4291,” which defines the basic notation for IPv6 addresses.
■Specific notation method of IPv6 address
There are two rules for expressing IPv6 addresses. It is as follows.
1. When the fields separated by “:” are all zeros “0000”, if there are two or more consecutive fields that meet this condition, “0” can be omitted and it becomes “::” Example: 0000 :0000→::
2. Example where leading zeros and consecutive zeros can be omitted in fields separated by “:”: 0db8→db8
Example: 0000:0000→0:0
Based on these considerations, if we write Yahoo! JAPAN’s IP address “183.79.248.124” in decimal notation as explained in the above item “How to write an IPv4 address” as a hexadecimal IPv6 address, it becomes as follows.
| Yahoo! JAPAN IPv6 address notation | |
| IPv6 | 0000:0000:0000:0000:0000:ffff:b74f:f87c |
| Leading zero omitted IPv6 | ::ffff:b74f:f87c |
| Consecutive zero omitted IPv6 | 0:0:0:0:0:ffff:b74f:f87c |
What you can tell by IP address
The information actually obtained from an IP address is divided between the user side and the server side.
Information that users can understand
The user side is the user. Users can learn the following items, but none of them allow them to obtain personal information such as specifying their address.
Provider that the user has a contract with
One of the pieces of information that users can obtain from their IP addresses is information about their contracted providers. If you use a smartphone, you can also obtain information about your carrier. In the case of a corporation, you can obtain provider information, company name, organization name, etc. that provides Internet services for corporations.
router that connects the internet line
If you are using a home internet connection, you may be able to find out information about the nearest router. You can obtain the router information that is the exit point when connecting to the Internet.
User’s device environment
The user’s device environment can also be obtained from the IP address. You can obtain OS information (individual identification number), hardware information, PC monitor screen resolution, etc. of computers, smartphones, tablets, etc. You can also obtain information such as the type of browser that is viewing the website, cookie information, and the URL of the link source.
Information on the server side
The server side is the so-called provider side. Even on the provider side, detailed personal information cannot be obtained from the IP address. However, personal information can only be identified by the provider that manages the IP address.
As with the user side, the information that can be obtained from the IP address on the server side is limited, and is generally information about the provider connected to the Internet, information on the server’s hardware resources, and OS information.
2 types of IP addresses
There are multiple types of IP addresses. Here, let’s check two things: the global IP address and the private IP address. Both are essential IP addresses when using the Internet.
What is a global IP address?
As the name suggests, a global IP address is an IP address used to connect to networks around the world. When you connect to the Internet, you can send and receive data from anywhere in the world, because a global IP address is assigned to your device.
A global IP address is assigned to prevent sending mistakes. It is unique in that it is the only one of its kind in the world. So, how are global IP addresses managed and allocated?
The organization that allocates them is ICANN. It stands for “The Internet Corporation for Assigned Names and Numbers” and is a private, non-profit corporation established in the United States in October 1998. In addition to IP addresses, we also make adjustments by allocating domain names, protocol port numbers, etc.
IP addresses are managed globally by ICANN, and are allocated by ICANN to Japan Network Information Center (JPNIC), a Japanese management organization, and used by JPNIC via each Internet service provider (ISP). allocated to the user.
JPNIC is an organization that supports the smooth operation of the Internet, and manages number resources on the Internet such as IP addresses and AS numbers in Japan, investigates and researches Internet infrastructure technologies, and promotes the use of the Internet through events and various media. We make various adjustments from a neutral standpoint, provide experimental environments, etc., collect and provide information on Internet-related policies and governance, and participate in deliberations.
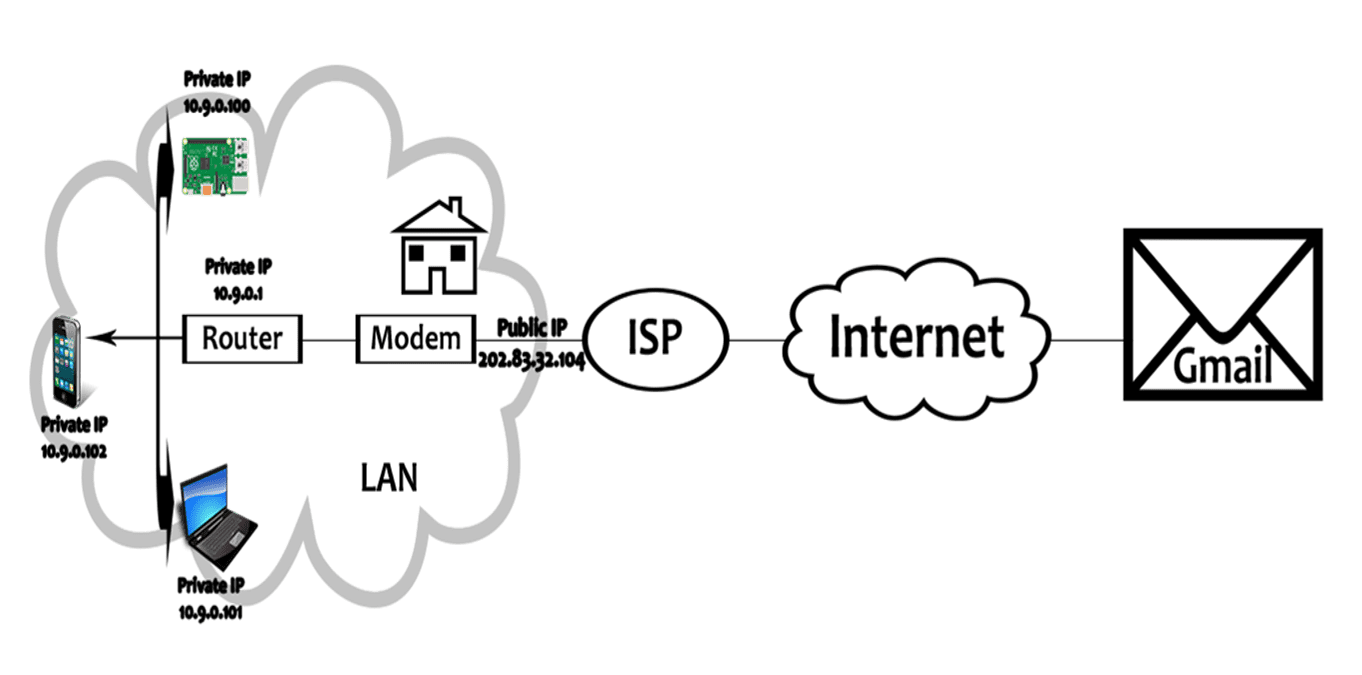
What is a private IP address?
On the other hand, a private IP address is an IP address that is used only within the range of a specific network, such as your home or office. Also called local IP address.
Unlike a global IP address, it is for identification within a limited network, so the same number may be used in other networks. Usually, a router allocates a local IP address to your computer or smartphone.
Connection between global IP address and private IP address
In fact, to connect to the Internet on your computer, you use both a global IP address and a private IP address. You cannot connect to the Internet with just a private IP address.
The router will allocate a private IP address. Since the router itself has a global IP address, you can connect to the Internet via that router. In other words, it is connected to the Internet via a private IP address and through a router with a global IP address.
How IP addresses are allocated
Next, let’s take a look at the mechanism by which IP addresses are allocated. There are two types of IP address allocation methods: dynamic type and fixed type. These are respectively called “dynamic (variable) IP addresses” and “fixed (unchangeable) IP addresses.”
What is a dynamic (variable) IP address?
A dynamic (variable) IP address is one in which your ISP automatically assigns you a new IP address each time you connect to the Internet. The IP address is not fixed, but changes dynamically.
A dynamic (variable) IP address changes its number after a certain amount of time or whenever you disconnect from the Internet. In most cases, the default initial settings are such that a dynamic (variable) IP address is automatically allocated, so no special connection settings are required.
For example, when connecting to the Internet using a computer or smartphone on a daily basis, a router is often used, and in that case, a dynamic (variable) IP address is assigned. Dynamic (variable) IP addresses are also used in public Wi-Fi.
What is a fixed (unchangeable) IP address?
On the other hand, there are cases where a fixed (unchangeable) IP address is assigned, which is a fixed number that does not change. This is for when you always want to connect with the same IP address. Dynamic (variable) IP addresses can be problematic because they are not always the same and change periodically.
So, what kind of cases do you have trouble with? A simple example is when a company wants to ensure that only certain authorized users’ devices can access their internal systems. At this time, suppose you obtain the IP address of the employee’s computer and allow access only to the device with that IP address.
But what if your IP address changes every time your employees connect to the Internet? Unable to identify employee. Therefore, a fixed (unchangeable) IP address that does not change is required. For example, it is used for remote work when employees access the company from home. The following are common scenarios in which fixed (unchangeable) IP addresses are used.
Fixed (unchangeable) IP address usage scenarios
The main usage scenarios for fixed (unchangeable) IP addresses are as follows.
When using internal systems from outside the company
When employees want to access internal systems from outside the company, a common method is to have them log in with a user ID and password. In addition, set fixed (unchangeable) IP addresses on employee computers and configure internal systems to only accept access from authorized IP addresses. This will further improve security.
When remotely monitoring images from an internet camera using a computer
Internet cameras for security purposes are connected to the Internet, so you can view the camera footage on your computer. The Internet camera also requires an IP address, but a fixed (unchangeable) IP address is used. For security reasons, it is necessary to ensure that only authorized fixed (unchangeable) IP addresses can be viewed.
When remotely operating IoT devices, etc.
Recently, technology for operating IoT devices from remote locations has advanced. If you want to connect IoT devices to the Internet and remotely control them from a computer or smartphone, it is common practice to assign a fixed (unchangeable) IP address to the IoT devices.
When using cloud services
In recent years, companies often use cloud services to conduct business, but in order to ensure security when accessing those cloud services, they set a fixed (unchangeable) IP address as the global IP address and use cloud services. Restrict access to the Service to that IP address only.
Fixed (unchangeable) IP addresses like this are available with most ISPs, but they are often included in optional plans. Therefore, when using a fixed (unchangeable) IP address, it is necessary to change settings from a dynamic (variable) IP address. In addition, the application and setting methods and additional fees vary depending on the ISP.

How to check your IP address
To understand more about IP addresses, let’s check the IP address of your computer.
How to check your global IP address
Currently, the quickest way to check the global IP address of the Internet you are connected to is to access a web service.
If you search for keywords such as “Global IP address confirmation” on Google, you will find a website that allows you to check your global IP address just by accessing it. When you access it, you can check your global IP address as well as your ISP.
How to check your private IP address
We will show you how to check your private IP address when you are connected to the Internet using a Windows computer. You can check it using the following two methods on the computer you are currently using.
Confirmation method using Windows “Command Prompt”
Type “command prompt” or “cmd” in the search box at the bottom left of your Windows desktop. After that, a command prompt will start, so enter “ipconfig” or “ipconfig/all”.
Then, a list of information about network connections will be displayed, so check the “IPv4 address” column. The number “XXX.XXX.XXX.XXX” is your private IP address.
How to search in task manager
Similarly, type “task manager” in the Windows search box to start Task Manager. Select “Performance” from the multiple tabs at the top. Click on the item “Wi-Fi” or “Ethernet” in the list on the left, and check the numerical value of the item “IPv4 address” among the displayed contents on the screen on the right.

Issues surrounding IP addresses
There are some issues with IP addresses. I would like to introduce two main issues.
IP address exhaustion problem
One is the problem of IP address exhaustion. I mentioned earlier that IP addresses are assigned 4 sets of numbers from 0 to 255. Actually, this is a protocol named “IPv4”. It is possible to manage over 4.294 billion IP addresses.
However, it is said that the number of approximately 4,294 million or more is actually at risk of running out of IP addresses. The background to this is that demand for the Internet has further expanded due to the spread of smartphones and the evolution and spread of IoT devices.
As a countermeasure to this problem of IP address depletion, a newly agreed upon protocol is the use of “IPv6”. IPv6 is a method of notation using 8 sets of 4-digit alphanumeric numbers. Let’s compare it with IPv4.
As you can see, the notations for IPv4 and IPv6 are completely different. IPv6 can allocate up to 340 IP addresses (340 trillion x 1 trillion x 1 trillion), which is a huge increase compared to IPv4.
IPv6 is already in use, but it is not yet widely used. The reason for this is that there are several conditions for using IPv6, and there are few cases where these conditions are met. The conditions for using IPv6 include that the Internet line supports IPv6, that the ISP provides an IPv6 connection, and that the router supports IPv6.
IP-related cyber attacks
Another issue is the existence of IP-related cyber attacks. A cyber attack method called “IP spoofing” has become a problem in recent years.
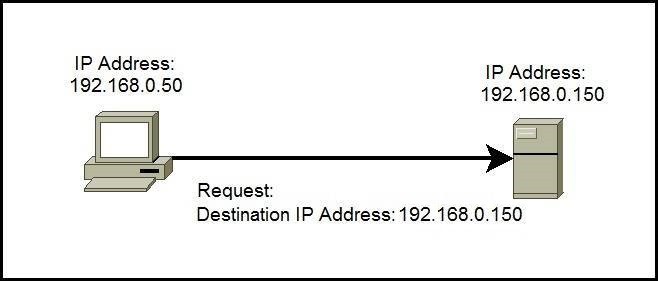
What is IP spoofing?
IP spoofing is a type of cyber-attack in which someone disguises their own IP address to commit fraud or attacks. It comes from the English word “Spoof”, and has the meaning of “to deceive/katsugu” in Japanese. In other words, it is a type of spoofing that involves spoofing IP addresses to commit malicious acts.
IP spoofing attack example
A common method is to rewrite the source IP address in the header of communication packets, attempt to establish a communication connection using that spoofed packet, and break through access using the fake IP address. Let’s take a look at an example of how someone can impersonate someone to commit malicious acts.
■Attack example 1:
When IP addresses are restricted when accessing internal systems or websites, attackers disguise themselves as authorized IP addresses to breach the IP address restrictions and conduct attacks or steal personal information. or deface websites to direct users to phishing sites.
■Attack example 2:
Use someone else’s IP address to impersonate another person and commit malicious acts.
IP spoofing issues
A major problem with IP spoofing is that it is difficult to identify the source of the attack. This is because the only information left in the attack log is the spoofed IP address, so there is no information about who was behind the spoofing.
As a means of large-scale cyberattacks such as “DoS attacks” and “DDoS attacks” that disrupt services by concealing the source of the attack and intentionally placing an excessive load on resources such as servers and networks. It is said that it is often incorporated. In addition, it is said that preventive measures are also difficult because it is difficult to protect against it by filtering by IP address.
IP spoofing prevention measures
One way to prevent IP spoofing is to avoid using IP address-only authentication. This includes password authentication, the use of authentication keys, and the combined use of MAC addresses. Combining multiple authentication methods increases the possibility of preventing intrusion.
There are also methods such as encrypting communication to make the information unreadable, and using a firewall to detect strange behavior.
Can an individual be identified by an IP address? Is there a risk?
Since IP addresses are assigned to personal computers and smartphones, there may be concerns that if they are known to a third party, they may be able to identify you.
With the spread of telework, the number of cases in which fixed (unchangeable) IP addresses are used is increasing, and there may be concerns that if those fixed (unchangeable) IP addresses are leaked, people will be able to find out who and where they are. . However, since IP addresses are a type of public information, it is said that there is no major risk even if they are known to a third party.
Additionally, it is generally accepted that personal information will not be leaked from IP addresses. Only your ISP or telecommunications carrier can identify you from your IP address. ISPs and telecommunications carriers do not disclose personal information, except in special cases such as when an incident occurs and a court orders disclosure. Therefore, there is no risk of anyone finding out that the person using this IP address is Mr. ○○ who lives in ○○.
Although an individual cannot be identified by an IP address, there is some risk.
However, if you are not careful, you may be caught unawares. Please be aware of this risk. First, if your IP address is tracked, your actions on the Internet may be known. For example, if a victim posts slander on an anonymous message board, the victim may ask the company operating the message board to ban the user’s IP address from writing.
The type of action taken will vary depending on the bulletin board operating company, but such problems may occur. Although it is not possible to determine a name or address from an IP address, it is possible to determine whether it is the same user. Additionally, if your IP address information becomes known to a malicious third party, it may be used for unauthorized access or cyber attacks.
First of all, you should know that the IP address can tell you to some extent the area you are accessing, such as “Minato-ku, Tokyo.” IP addresses that can identify location information in this way may be used for marketing and promotional activities such as advertising distribution and pricing. If this happens, the information is useful to companies operating such businesses, so there is a risk that it will be misused, such as by illegally obtaining IP addresses and selling or transferring them.
There are also risks like this. Since it is possible to know the ISP that an individual uses from the IP address they use, there is a possibility of falling victim to phishing scams that impersonate the ISP company. Although the general opinion is that there is no risk of personal information leakage with IP addresses, you should be aware that if they are misused, there is a considerable risk of getting into the troubles mentioned above. .
Personal information can only be obtained when making a “sender disclosure request”
Basically, you cannot get detailed personal information from the IP address, so if you want to get personal information, you have to make a request to disclose the sender. The request for disclosure is to request a provider to disclose the personal information of a specific user.
For example, online, if you are damaged by slander on SNS or the like, you can request a claim for damages by requesting the sender disclosure and obtaining your personal information.
However, if you make a request to disclose the sender, no personal information will be disclosed. There are conditions for the call for disclosure to be disclosed, and it is generally limited to “when it is determined that there is an infringement of rights” or “when there is a legitimate reason for disclosure”. It is not easy to disclose it, so it is important to clearly indicate a solid disclosure reason.
To hide the IP address
Hiding the IP address and protecting so that it is not seen by others, it is desirable to actively do it because it will protect personal information and identity information. The following methods are listed.
Use of proxy server
A proxy server refers to a server installed between the user and the server. Proxy means “agency” and plays a role in relay both communications. This proxy server exists in various places and comes with a huge IP address pool.
Every time a user connects to online, you can access it in a different route from the previous time by via a proxy server. In other words, every time you use an IP address different from a different proxy server, you will hide the IP address as a result.
Use of VPN
Using a VPN service is also an effective way to hide the IP address. The VPN service is a virtual communication network that can be used only by contractors.
If you use this virtual communication network to perform tunneling (the opening of a virtual direct line between two bases), you can protect information from a third -party tampering and eavesdropping. Every time you connect to online, you can borrow a new IP address, so you will hide the real IP address.
summary
- IP is an abbreviation of Internet Protocol (Internet Protocol) and is the “Communication Terms”. The Internet network requires a common communication rules for communicating with equipment and equipment. In order to connect to the Internet, an “IP address” is required to assign a number to identify individual devices such as personal computers, smartphones, and tablets. The IP address is like an address on the network to identify equipment on the network.
- The IP address has a global IP address and a private IP address, the router allocates a private IP address, and the router itself has a global IP address, so it can be connected to the Internet via the router.
- There are two ways to assign IP addresses: dynamic and fixed types. The default is a dynamic (variable) IP address, and the fixed (unchanged) IP address is used according to the usage scene.
- The challenges of IP addresses are cyber attacks that impersonate the IP address depletion and IP addresses.
- Since the IP address is a kind of public information, it is said that there is no major risk even if it is known to a third party. In addition, it is common to see that personal information is not leaked from IP addresses. However, the same user may be known by the actions on the Internet, and there is a risk that if it is misused, it will be involved in trouble because it can understand the access area to some extent.





