If you are using the Internet, you may have heard the term “TLS” as a communication encryption method. TLS is a type of protocol, but it is different from the commonly heard SSL and HTTPS.
In this article, we will explain the overview of TLS, the difference between SSL and
HTTPS
, and the characteristics of TLS. We will also introduce how TLS works and how to implement it, so please refer to it.
What is TLS?
TLS (Transport Layer Security) is a protocol for encrypting data communication over the Internet and increasing security. TLS is responsible for protecting the transmission and reception of data, and can protect your data from man-in-the-middle (third party) attacks.
Specifically, TLS has functions such as public key authentication, common key encryption, and hashing, which prevents eavesdropping, spoofing, and security interference.
What is the difference between TLS (Transport Layer Security) and SSL?
Earlier, I gave an overview of TLS. By the way, how are TLS and SSL different? In conclusion, although TLS and SSL (Secure Sockets Layer) have the same basic purpose, they are different protocols.
SSL is the older version and TLS is the improved version of SSL. TLS has enhanced security and improved performance, and has the advantage of ensuring more secure communication compared to SSL.
Additionally, a serious vulnerability called POODLE (Padding Oracle On Downgraded Legacy Encryption) was discovered in SSL, and TLS was developed in response to this.
On top of that, TLS has succeeded in improving security by introducing more secure cipher suites and protocols. Therefore, we recommend implementing TLS for more secure communication.
What is the difference between TLS (Transport Layer Security) and HTTPS?
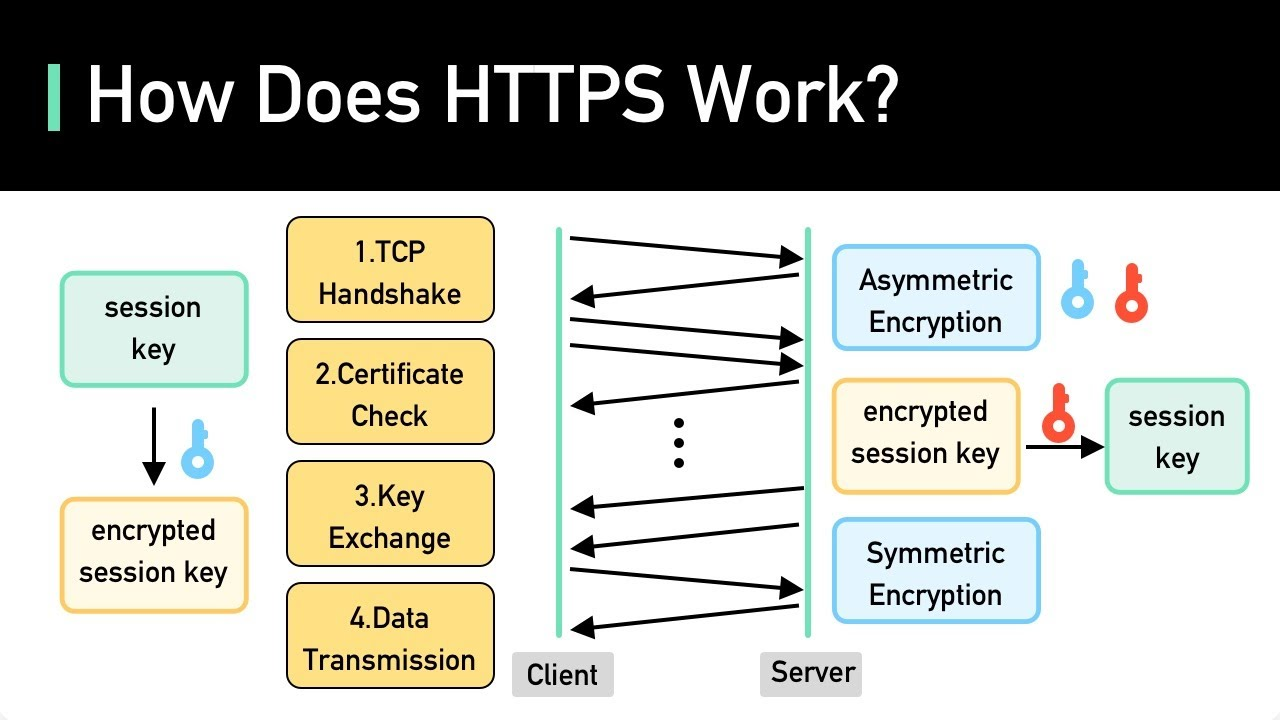
Next, let’s look at the differences between TLS and HTTPS. TLS is part of a communication protocol, and HTTPS (HyperText Transfer Protocol Secure) is one way to use TLS to achieve secure communication on a website.
Therefore, HTTPS is not a protocol. Additionally, HTTPS uses TLS to ensure security when browsing the web and to prevent data eavesdropping and tampering.
HTTPS indicates that the destination web
server
communicates using TLS.
Google, which has a large share of the search engine market, is increasingly displaying non-HTTPS communications as “not secure” and alerting website operators and users.
If you are using HTTP, there is a high possibility that your data will be intercepted or tampered with by a third party. When using
a search engine
yourself as a user, make sure that “https://” is added at the beginning of the URL, and make sure that the communication is secure before using it. Sho.
Characteristics of TLS (Transport Layer Security)
So far, we have explained the overview of TLS and the difference from SSL. Let’s take a look at three characteristics of TLS.
I will explain each in turn.
Encryption
TLS is characterized by high encryption. Data is encrypted to prevent third parties from decoding it, making it possible to protect sensitive information and ensure privacy. These encryption systems use a function called “public key encryption,” which has the advantage of providing stronger security measures than SSL.
certification
TLS also has authentication functionality. It mainly authenticates the communication partner, allowing the client and server to reliably confirm the authenticity of the other party. If authenticity can be confirmed, man-in-the-middle attacks such as eavesdropping and tampering can be prevented, and certificates can be used to confirm the identity of the communication partner, enabling secure communications.
safety
Finally, TLS is also highly secure. TLS is a security protocol that ensures data integrity and ensures that the data has not been tampered with. This has the advantage of maintaining the validity of data and allowing communication to be carried out in a state where the operator and the communicating party can trust it.
Additionally, TLS is regularly updated to address new vulnerabilities. Therefore, it is important to always use the latest version rather than just implementing TLS.
What is a TLS certificate?
When using TLS, it is also possible to issue a TLS certificate. A TLS certificate is a digital certificate used to verify the identity of a website or server. Certificates are issued by a trusted third party (certificate authority) and verified by the client browser. This makes communications more secure and reliable.
The contents of the certificate include the public key, certificate owner information, certificate issuer information, etc. By looking at this information, you can confirm the legitimacy of the person you are communicating with.
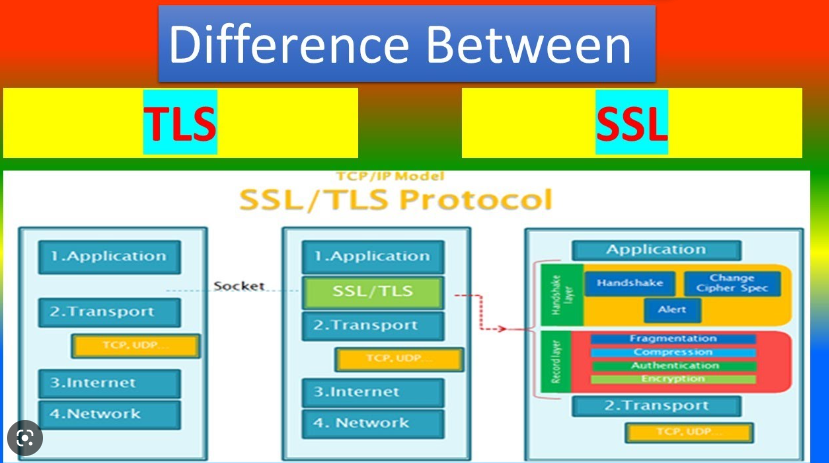
How does TLS (Transport Layer Security) work?
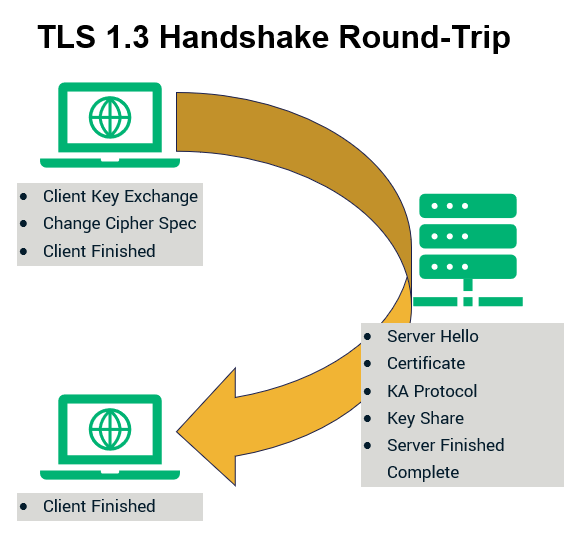
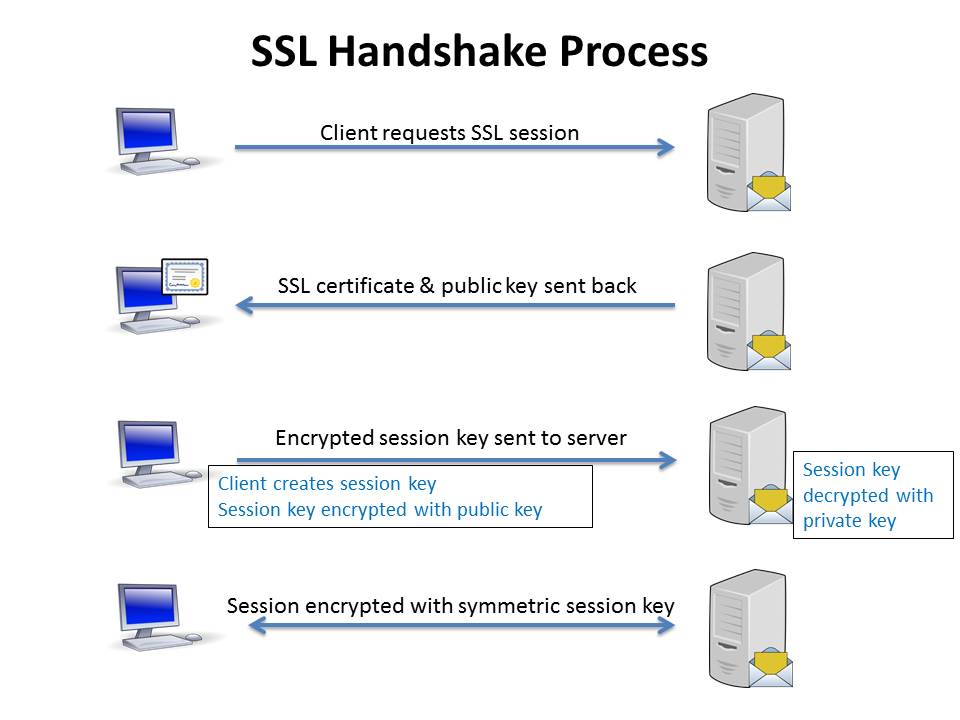
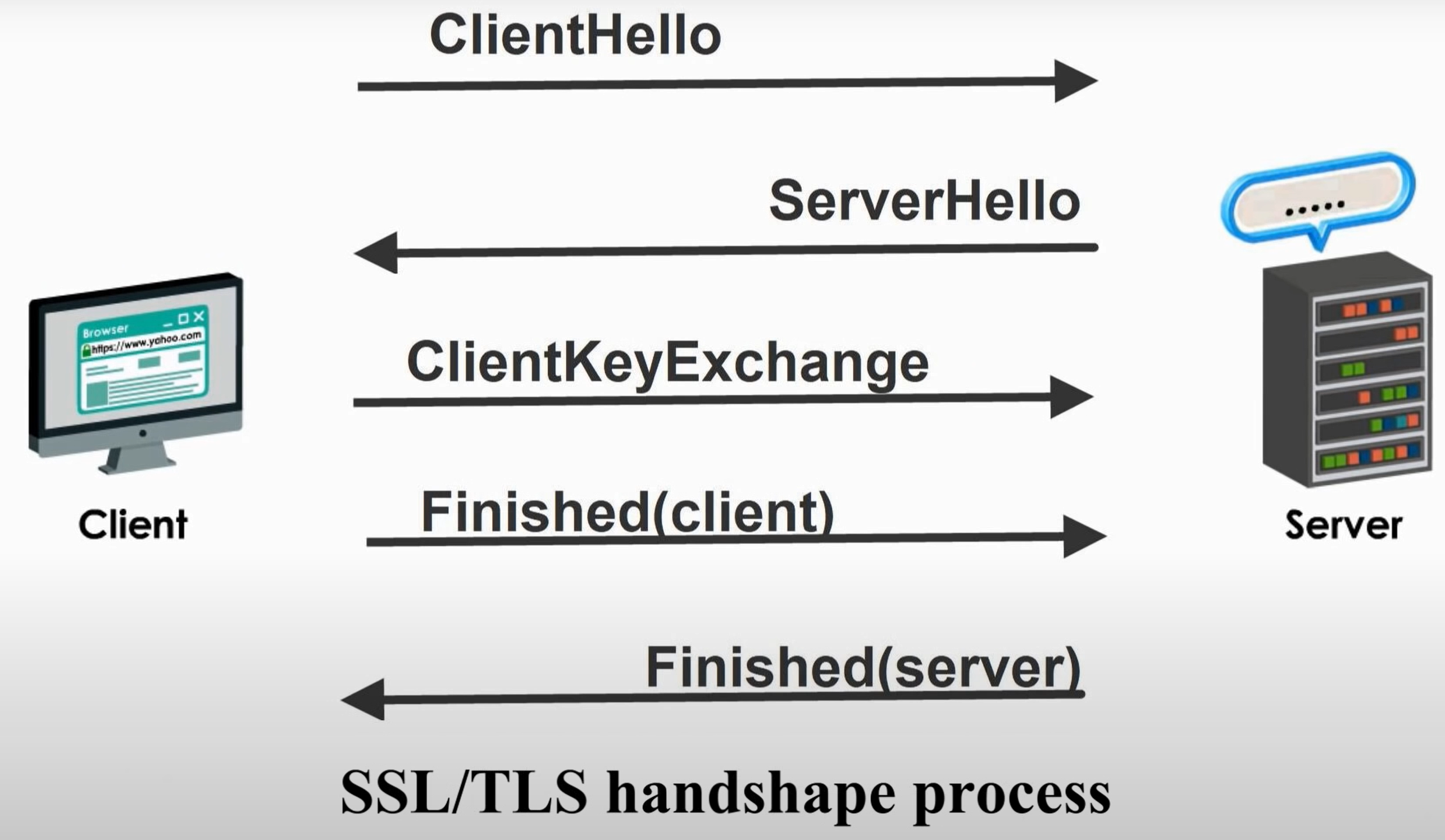
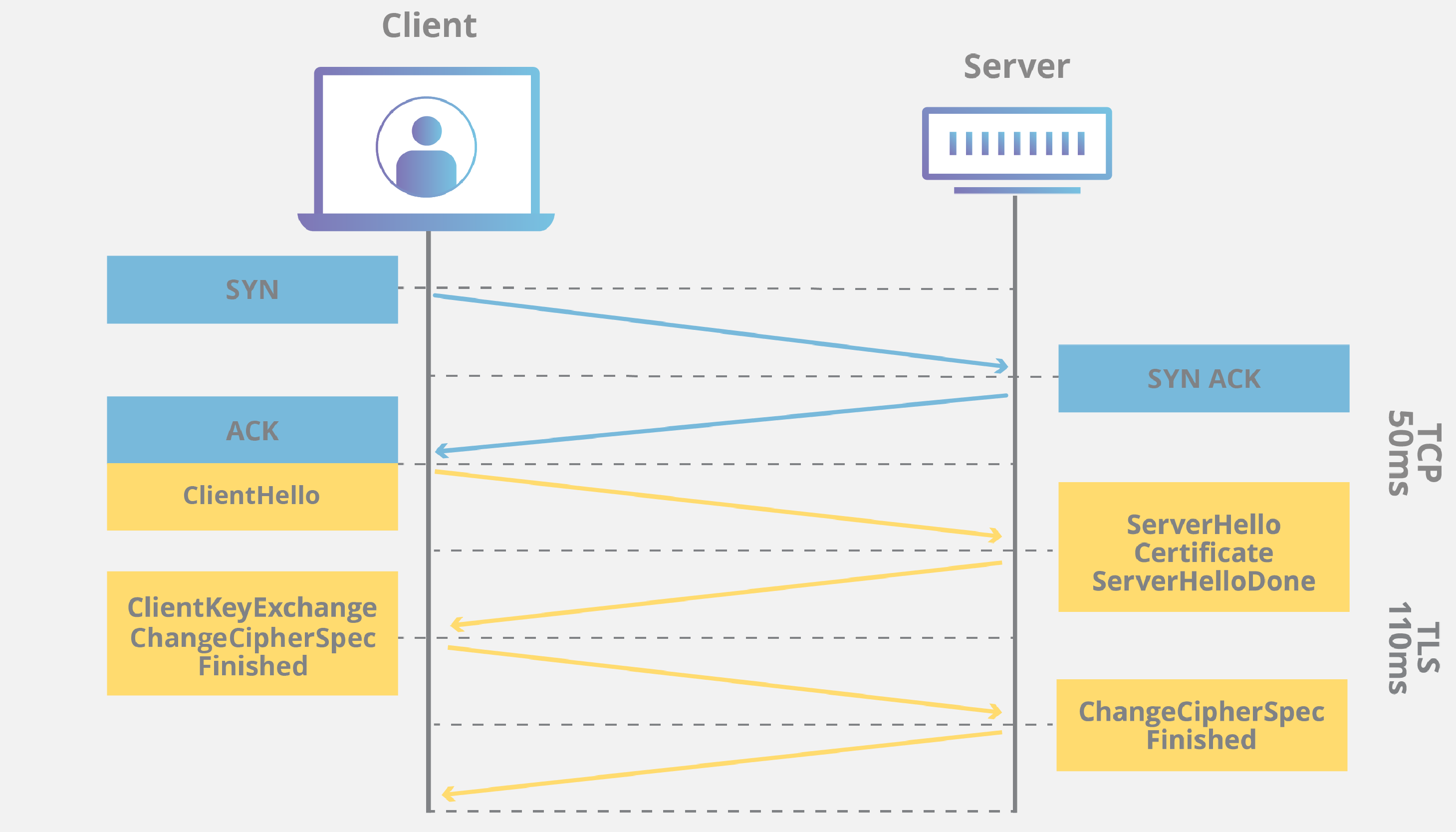
The TLS mechanism is characterized by consisting of handshake, encryption, and authentication phases. The handshake verifies the communication partner and sets security parameters, and the encryption encrypts and decrypts data. Additionally, authentication uses certificates to authenticate the other party.
In other words, security is confirmed through three steps: handshake → encryption → authentication. In a handshake, the client sends a connection request to the server, and the server returns a public key and certificate. The client then uses this information to verify who it is communicating with, and a common cipher is created.

Why should companies use TLS (Transport Layer Security)?
So far, we have explained TLS and SSL, but which one should companies use? In conclusion, you should use TLS when possible. That’s because businesses can benefit from using TLS, including protecting client data and sensitive information, improving reliability, and ensuring legal compliance.
In addition, by implementing TLS, companies can strengthen their security measures and gain the trust of their customers.
Especially in this day and age where
online
transactions via the Internet are increasing, highly secure communications are essential. Of course, SSL is also highly secure, so this is not a problem, but considering that the Internet will continue to develop further, it would be a good choice to introduce TLS at this stage.
Explaining how to introduce TLS (Transport Layer Security)
There are multiple ways to implement TLS. From here, we will explain in detail one example of how to implement TLS.
Issue a CSR (Certificate Signing Request)
First, you need to issue a CSR to obtain a TLS certificate. A CSR (Certificate Signing Request) is characterized by containing all the information necessary for a server to request a certificate from a certificate issuing authority (CA).
Generate a CSR by following the steps below.
By following the above three steps, the CA will approve the CSR and issue a TLS certificate.
Install certificate on server
Next, once your CSR is approved, your certificate authority will provide you with a TLS certificate. By installing this TLS certificate on the server, highly secure communication will begin.
Note that the steps to install the certificate on your server vary depending on the web server you are using, but the general steps are as follows:
Regarding the third step, “Configure to use a certificate,” the steps differ depending on each web server. Many web servers have TLS implementation manuals available. If you still have questions, please contact your server’s customer support.
summary
In this article, we have explained the basic mechanism of TLS and its differences from SSL. TLS is an essential protocol for ensuring the security of Internet communications and is of great importance to businesses and website operators.
Using TLS also helps ensure the safety of connecting customers. However, even after installation, updates will be made regularly, so be sure to always update to the latest information.
First of all, why not refer to this article and proceed with the introduction of TLS?

